Do You Know What Terror Groups Use As Greatest Weapon?
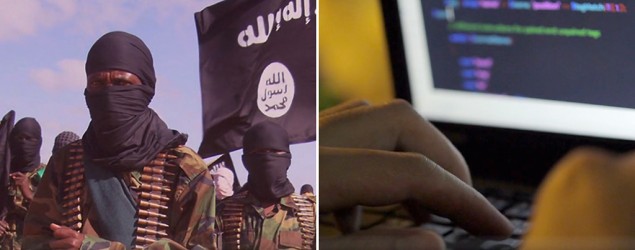
Terrorists in the modern age have a tool in their arsenal that allows them to operate under the radar: technology.
After a series of unexpected and devastating attacks, counterterrorism officials believe that it’s getting harder to track ISIS because they “go dark” through the use of encryption messaging and apps.
The
act of encryption, when a message is encoded so others can’t read it,
is centuries old.
Think of Egyptians and cryptography or Julius Caesar
and the Caesar cipher.
But now, the Internet and tech advancements have propelled encryption
into the digital age. Most encryption programs transform information
into a series of letters and numbers, which can only be opened with a
key. One message can have multiple codes, each with a different key,
making it a nearly impossible to crack.
We
use encryption often in our daily lives when we go online, like when we
shop or bank. But databases exist that can be used to really cover a
person’s tracks. Software like Tor
— originally developed by the U.S. government to protect private
intelligence information — uses an anonymous network of servers to
create a space on the “dark Web” where people with access are
untraceable online.
Encryption apps like Apple’s iMessage, WhatsApp, Signal and Telegram use end-to-end encryption,
meaning only the people sending and receiving the messages can see
them. Many of these apps have settings that allow messages to disappear
after a set time or to prevent messages from being forwarded.
Terror groups have encrypted their information for years, but recently, the technology has become more secure and accessible. Government intelligence agencies
want tech companies to leave a flaw, or “back door,” in their programs,
so they have a way to decrypt messages if needed. But cybersecurity
experts warn against this, saying it leaves the products vulnerable to
hackers.
Even
with encrypted communication, law enforcement and intelligence agencies
are able to gather critical clues and information, but it can be more
difficult. I think everyone needs to know about encrypted messaging apps.
No comments:
Post a Comment